Recently I had a bad memory module in my main storage system which is also the backup target of many of my systems. To be on the safe side, I validated all backed up files against their origin via checksums. Interestingly, multiple systems showed differing checksums for all DejaVu font files, i.e. the files in the backup did not match those in the system. Clearly, this was not caused by the bad memory module. It looked very much like a systematic issue.
Read MoreTinkering with the StarFive VisionFive 2
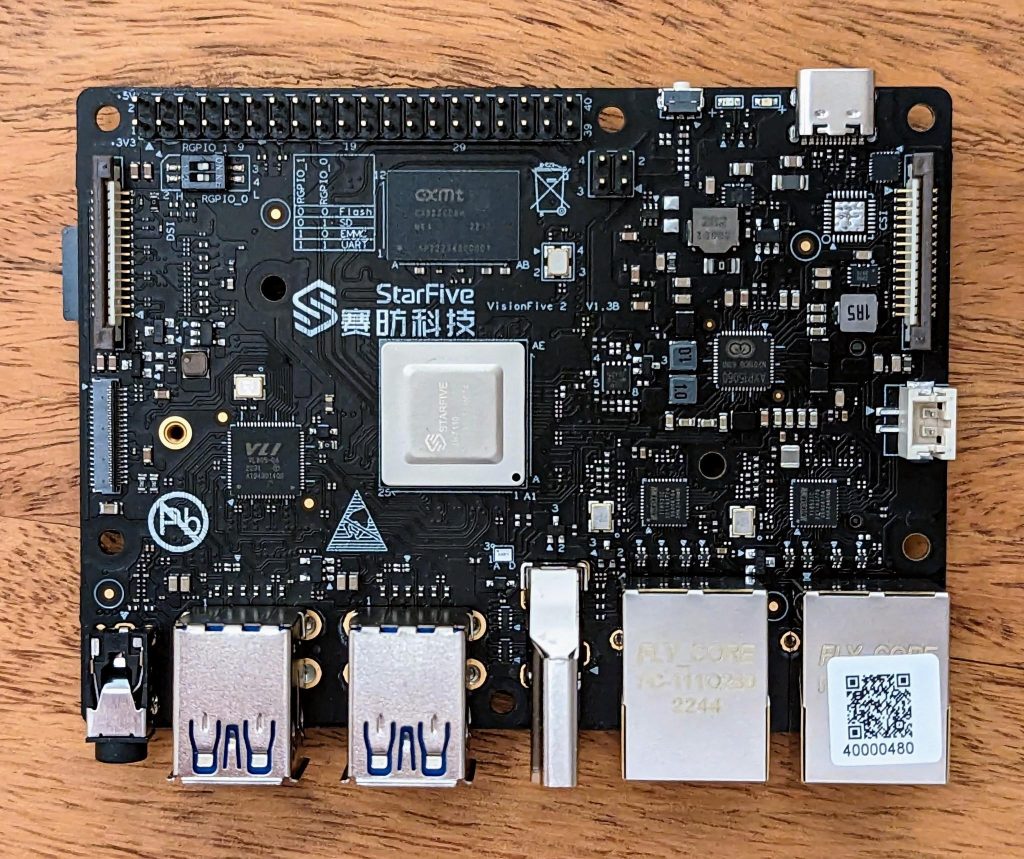
With RISC-V getting more and more attention, I was curious and got myself a StarFive VisionFive 2, a single board computer equipped with a SiFive JH7110 SoC which implements the RV64GC ISA. While the performance is not on par with ARM SBCs yet, the overall experience has been quite good so far. In this article, I share some of my experiences with it.
Debugging a flaky cpu steal time counter on a paravirtualized Xen guest
I recently noticed a strange phenomenon on a Debian Stretch server running as a paravirtualized guest on a Xen host: top showed the CPU either be 100% idle or 100% stolen. User, system, nice and waiting times were stuck at 0%. I cross-checked with vmstat and it showed 0% for all cpu time counters. Both tools are getting their information from /proc/stat which looked like the following:
cpu 5322 0 4376 12720669 37879 0 59 1198368772563 0 0 cpu0 5322 0 4376 12720669 37879 0 59 1198368772563 0 0 ...
The third to last value is the steal time, denoting “stolen time, which is the time spent in other operating systems when running in a virtualized environment” [procfs(5)]. This value looked way too high and, in particular, it was counting backwards. So, if I wanted to put this system into production, some debugging was required before…
Migrating from ownCloud 9.1.6 to Nextcloud 10
If you are stuck with PHP 5.4 (e.g. because you are still running Debian Wheezy) and want to migrate from ownCloud to Nextcloud, you are probably facing a minor issue. Nextcloud 11 and newer require PHP 5.6 so you have to stick to version 10 instead. Nextcloud 10 reached its end-of-life with version 10.0.5, which internally corresponds to ownCloud version 9.1.5. The most recent version of ownCloud 9 is version 9.1.6 though, so when trying to migrate to Nextcloud you will face the following error:
Downgrading is not supported and is likely to cause unpredictable issues (from 9.1.6.2 to 9.1.5.2)
Looking at the git commits between ownCloud 9.1.5 and 9.1.6 shows that there were no changes to the database layout. So, as a workaround, you can just edit your config/config.php and set version to 9.1.5.1 or lower. Afterwards, you should be able to run the normal upgrade procedure.
Fixing Roundcube’s command execution vulnerability in Debian Wheezy
Recently a quite serious vulnerability (CVE-2016-9920) in Roundcube was reported. Until now (7th Dec) this vulnerability is unfixed in Debian’s roundcube packages (see the corresponding entry in the Debian Security Tracker).
The upstream patch is not directly applicable to version 0.7 which is used in Debian Wheezy but with a little modification it is. Following you find a corresponding patch*.
Read More
Setting up Xilinx development tools on Debian
Debian is not a supported system for running the Xilinx developments tools. That does not mean you cannot use them on Debian. Here is a quick overview over the necessary steps to get them running on Jessie.
Read More